What We Do for Continuous Monitoring
What We Do for Continuous Monitoring: Protects infrastructure with real-time threat intelligence monitoring
Xcitium cWatch is a comprehensive continuous monitoring solution for internal and cloud network security that is tuned to detect threats before they can affect your servers, databases or critical infrastructure. cWatch provides continuous monitoring and reporting of network, system, user activity and data access in combination with extensive analysis and correlation capabilities. The Xcitium breach and threat detection system follows a process to gather all data, including sources from the endpoint client network, and analyzes them against indicators of compromise (IOCs), using both data analysis and human analysis techniques.
What We Do for Continuous Monitoring: Xcitium Breach And Threat Detection Process
Simply by gathering logs from Advanced Endpoint Protection provides enterprises with extensive visibility over endpoints, files executed or in transit, the files’ verdicts and relevant interactions. 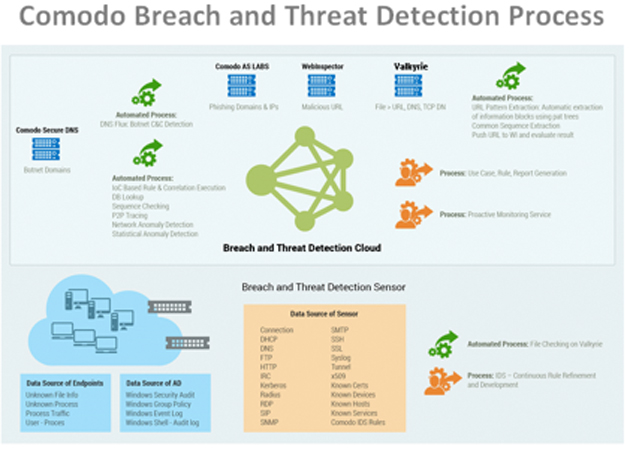
What We Do for Continuous Monitoring: ENDPOINT DATA IS ANALYZED AGAINST INDICATORS OF COMPROMISE
- Unusual Inbound/Outbound Network Traffic
- User Account Activity Anomalies
- Geographical Anomalies
- Authentication Anomalies
- Anomalies Specific to Backend Applications
- Web Traffic Anomalies
- Detection of Autonomous System Behavior
- Malware File Checking
- Port-Application Traffic Anomalies
- Suspicious Registry Or System File Changes
- DNS Request Anomalies
- Mobile User Profile Anomalies
- Signs Of DDoS Activity
- Long-Term Trending
CONTINUOUS MONITORING OF INTERNAL AND CLOUD NETWORK SECURITY
The Xcitium Security Operation Center (CSOC) provides breach prevention and threat detection delivered as a managed service (SaaS). As part of the managed service delivery, the CSOC is responsible for the monitoring and assessment of any advanced threats that target enterprise network assets and cloud-deployed applications along with accompanying underlying cloud infrastructure. With the extensive threat intelligence about emerging malware and threats from the Xcitium Global Threat Cloud, the CSOC provides an early warning and assessment of any malicious activity that target either of these environments. All of the services are managed by CSOC Centers in the US and EMEA.
NETWORK PLATFORM COMPONENTS:
- Endpoint Agent distributed via active directory (AD)
- AD Monitoring Agent
- Network Sensor
- Cloud Application and Big Data Platform
- Xcitium Threat Cloud: Domains, Valkyrie, and Phishing
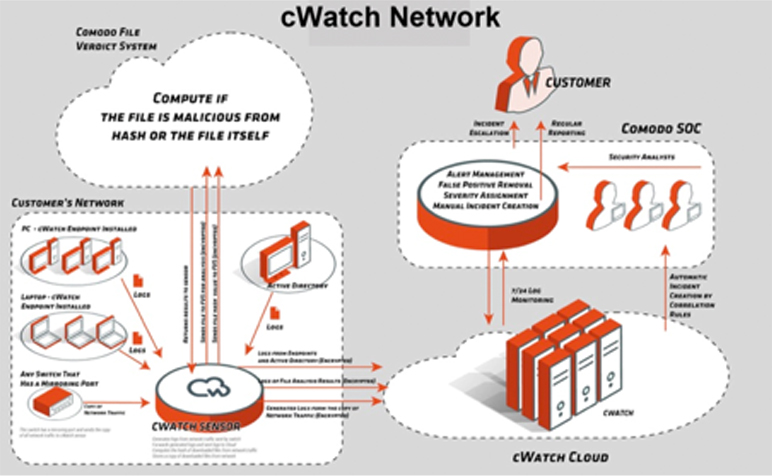
REAL-TIME THREAT INTELLIGENCE MONITORS:
- Malware (File)
- Insider threat (Users)
- Outside attacker (IP)
- Phishing domains (domain and email)
- Bot clients
COMPLETE NETWORK VISIBILITY
functions into one platform including network monitoring, application detection, full packet capture, intrusion detection, packet processing and protocol inspection. Real-time threat intelligence monitoring provides critical data on applications and infrastructure without affecting Network Performance. cWatch Network Sensor generates logs and information that are then normalized, classified and correlated by Xcitium SOC experts. Timely and meaningful alerts and reports are generated automatically without the arduous process of defining custom rules and queries resulting in: 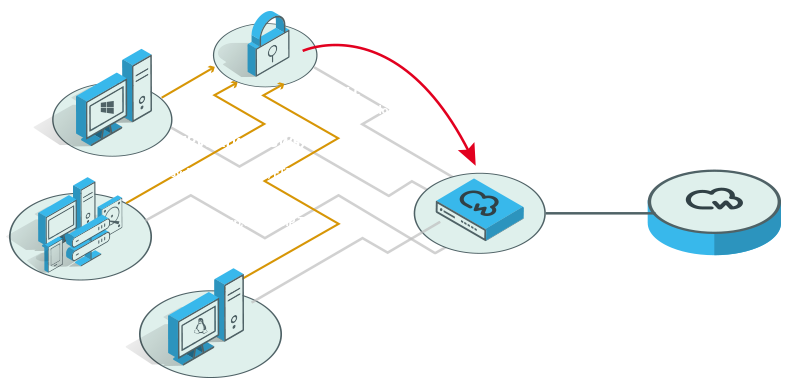
- Protection from the OWASP Top Ten list of vulnerabilities
- Immediate compliance to PCI DSS 6.6 without an application source code review or vulnerability assessment
- Visibility into the web server or application but also to any middleware applications, database access, configuration changes, server authentication, security logs, anomaly detection, incident response and alerting, as well as immediate protection from emerging threats by developing handcrafted security policies and signatures for your web site and applications.
- Prevention of infection and the damage from unknown (zero-day) threats




