Trojans Definition You Need to Understand
Updated on October 21, 2022, by Xcitium
In the world of technology, experts know very well that Trojan horse virus can resemble a regular software such as a utility, a game, and sometimes even an antivirus program. Often times, it is introduced using an email attachment or an infected website URL. That’s the reason why many ordinary users become victims of Trojan horse virus authors.
Users just suddenly experience unexpected changes to computer settings and unusual activity. Even when the user isn’t using the computer, a Trojan horse virus can be operating in the system’s background. That’s how an expert frames the trojans definition.
Some people may refer to a Trojan horse as a virus yet they’re technically different from each other. A computer virus can replicate itself, while a Trojan horse virus doesn’t have that ability. It doesn’t also have the ability to operate without an end user’s approval of computer activities.
In order to get users to execute the Trojan horse, cybercriminals exploit social engineering tactics. They use email accounts that send out email attachments forging an email of a legitimate business or the hackers disguise a Trojan horse virus as a free download. When the user finally decides to open the email attachment and download the attachment, the Trojan horse virus that is stored inside is transferred to the user’s endpoint. Then, the malicious code carries its designed feature to cause problems to the end user.

Incidents that Prove the Trojans Definition
The Eurograbber
A sophisticated Trojan horse virus attack happened to over 30 banks in Italy, Spain, Germany, and Holland in 2012. The estimated stolen amount is 36 million euros from 30,000 innocent customers.
The thief used the Trojan horse virus called Eurograbber. It utilizes Zeus-in-the-Mobile Trojan (ZITMO) and the exploit was only detected in Euro Zone countries, but a variety of this attack could possibly affect banks in countries outside of the European Union (EU) as well.
The Zeus Trojan infects customer’s desktop or laptop when they unknowingly click on a malicious link in a phishing email, a spam email or perhaps using a general web browser. The malware is downloaded onto the customer’s computer. Then, when the customer encodes his/her bank account details, the Eurograbber Trojan blocks their banking session and injects a javascript into the customer’s banking page. The customer receives a message alert from the Eurograbber Trojan asking for a “security upgrade” and instructs them on how to proceed. The malware passes the bank customer’s mobile information to the cybercriminal’s computer for storage and uses on subsequent attacks.
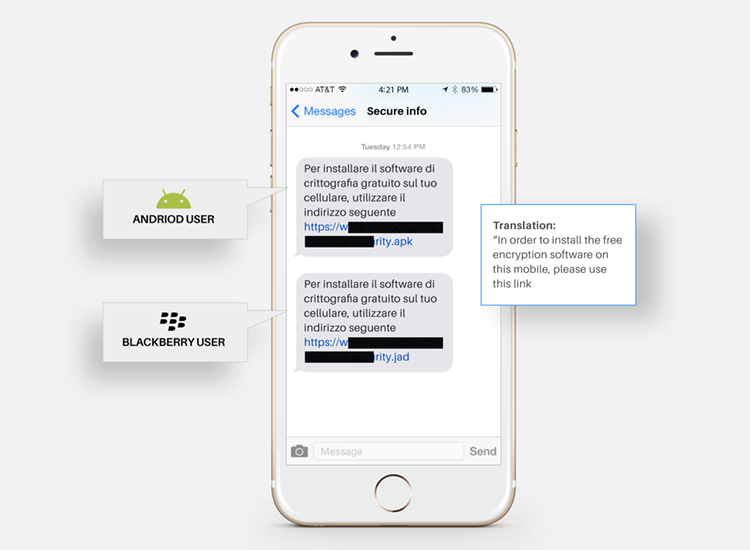
CryptoShuffler Trojan
In 2017, a Bitcoin Trojan named the CryptoShuffler stole 23 BT which cost around $140,000 from wallets during that time. The cybercriminals used the “clipboard hijacking” technique which replaces stored addresses with its own in the clipboard of a device
The CryptoShuffler exploits regularly used transaction processes. It monitors the clipboard of the targeted victim’s device. When making a transaction, the owner of the infected device copies a recipient’s wallet identification number. Then, it pastes the identification number in the destination address line in the software they use to do the transaction. The victim is unaware of the Trojan replacing their wallet address with the one the malware author owns.
They are not sending the money to the intended destination but to that of the cybercriminal when the victim pastes the wallet identification to the destination address line. This process only takes a second.
Storm Worm: 230 dead as storm batters Europe
In 2006, the Storm Worm was an unusually vile virus circulated the Internet with the subject line of “230 dead as storm batters Europe”. Since it presented itself as a news story, people opened the email and clicked on the link to the news story.
This was a big mistake on their part.
The Trojan horse virus, Storm Worm, infected computers and turned most of the endpoints into zombies or bots in order to spread the virus to more endpoints. It also sent a large amount of spam mail to other computers.
Storm Worm has been detected in more than 200 million emails and the actual damage it caused has yet to be determined.
Good thing there is a cybersecurity solution for Trojan horse viruses like the Storm Worm.
How Does AEP Work to Fight Trojans?
We hope by sharing Trojans definition with you and examples of the harmful strains of this kind of malware that you will be more prepared to handle these kinds of files. One of their key advantages is their ability to evade traditional signature-based antivirus scans.
The good news is that Xcitium Cybersecurity is offering the Advanced Endpoint Protection to protect your endpoints from malware. Advanced Endpoint Protection uses the Default Deny Platform™ to block bad files and automatically contain unknown files in a virtual container, using containerization technology.
The Xcitium VirusScope technology examines unknown files at the endpoint, for malicious behavior and actions. Valkyrie provides a cloud-based accelerated verdict in about 45 seconds, based on static, dynamic and even human analyst interaction. Malware files are removed, good files are allowed to run on the endpoint CPU and unknown files are contained in the lightweight virtual container on the endpoint and analyzed in real time.
You can expect Advanced Endpoint Protection to provide a report in a minute. It uses miniscule CPU resources and requires a computer footprint of just about 10 MB. The program provides complete security for both physical and virtual computers in all kinds of enterprises.
Related Sources:
Trojan Virus
Ransomware Protection
Ransomware Definition
Trojan Virus Removal





