What we do for usability
Updated on October 21, 2022, by Xcitium

Powerful Application Whitelisting
Almost everything that runs on an endpoint uses an application to do so. With Xcitium’s powerful application whitelisting capability, applications are automatically vetted against rigorous processes to ensure they are legitimate and safe before being allowed to run in your environment.
Xcitium’s extensive application whitelisting capabilities quickly identify good applications so they can run on the host machine. We are continuously tracking all the new applications from legitimate vendors. We know when there is a software update or a new application before our customers do. Other vendors can’t do application whitelisting at this level.
For example, Xcitium applies more than a dozen different processes for application whitelisting that are completely independent of each other. Two of these processes are related to our standing as the leading global certificate authority. We collect information from many different sources and use various methods to ensure we know that every application running on your endpoints has been given a trust verdict of good.
We follow legitimate software publishers to keep track of their applications. Because we trust these applications—they are known files and not malware—they don’t need to run in Secure Auto Containment. The result is there are no limits on usability. With this powerful whitelisting capability Xcitium is able to focus only on unknown or suspicious files and applications to prevent infection from malware including zero day exploits.
Secure Auto Containment Supports What We Do For Usability
Only Xcitium offers on-device, real time Secure Auto Containment of unknown files and accelerated trust verdicts from cloud-based analysis without negatively impacting system performance or end user productivity.
Xcitium Secure Auto Containment provides full Endpoint Protection with two layers of virtualization: the OS and the CPU. In this secure virtualized environment all unknown files or applications can be executed and used safely. During the short time that the unknown file is in containment, users can run the file or application safely until Valkyrie, Xcitium’s cloud-based file analysis system returns a trust verdict of good or bad. Good files are allowed to run on the endpoint and bad files are eliminated. If automatic analysis is inconclusive, files are analyzed manually for a trusted verdict.
Advanced Endpoint Protection shares threat intelligence immediately across the enterprise network to prevent infection at other threat vectors. Signatures—via application whitelisting and malware blacklisting—are dynamically updated as Xcitium’s trust verdicts convert unknown files to known.
What We Do For Usability: Xcitium’s CPU Enforced OS Virtualization
Secure Auto Containment™ of Unknown Files
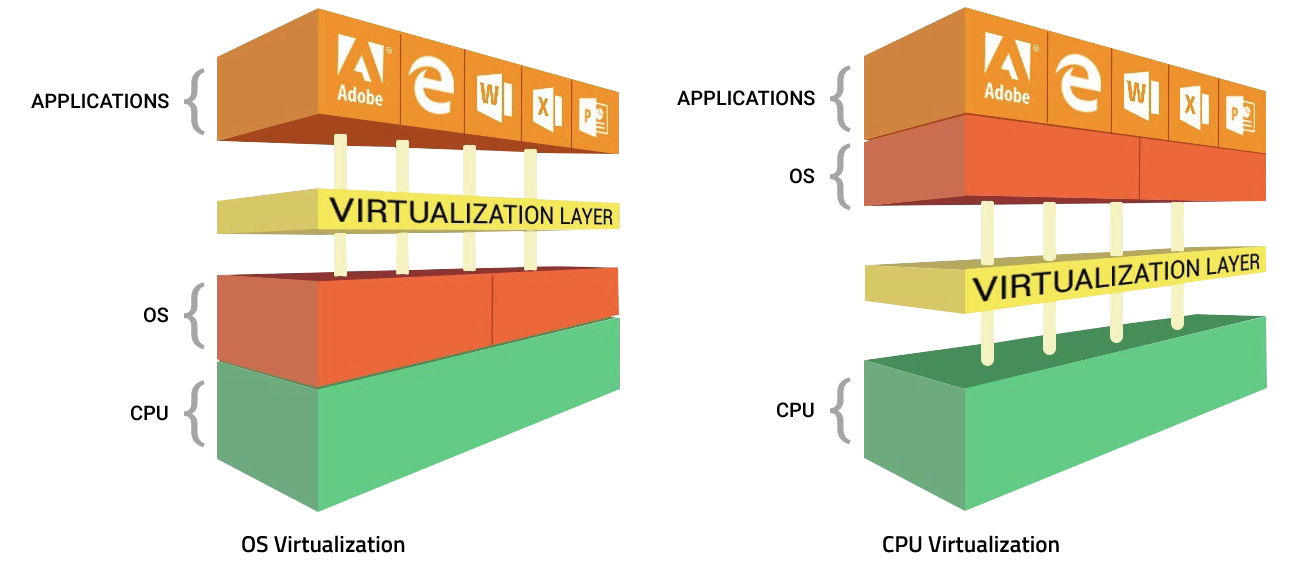
There are two virtualization methods available today, one at the OS and the other at the CPU. Xcitium uses both methods where available as some chip sets don’t support virtualization. Xcitium’s two layers of virtualization give our customers the best protection possible.
What We Do For Usability: Highly Efficient Virtualization at Two Layers
In some cases, virtualization is not supported by the CPU. This is why Xcitium focuses on the operating system (OS) as the constant for virtualization. Our innovative approach—Secure Auto Containment™–takes advantage of both OS and CPU virtualization. This gives our customers continuous security at the OS layer with added security at the CPU layer when supported.
What We Do For Usability: Lightweight – No Impact on CPU Performance
Xcitium’s Secure Auto-containment™ technology uses CPU-enforced OS virtualization with a single container (OS virtualization) model‚ that includes an exact copy of the endpoint machine including the kernel. This is one of the reasons startup performance is so fast in stark contrast to most sandboxes or containers that drain the CPU and slow down the system.
Xcitium Secure Auto Containment technology is extremely lightweight, has no CPU dependencies and is completely application agnostic. Malware or any other unknown process entering this virtualization environment cannot modify the hard disk, registry, or COM interface; therefore, preventing infection.
Optimum Security and What We Do For Usability
In the Xcitium virtualization environment‚ whenever a process or executable (PE) is run in containment (often referred to as “jailing”)‚ the analysis system sits between the PE and the shadow resources it calls-including CPU‚ memory‚ registry‚ file system and more. If the PE turns out to be malicious code and attempts to exploit the machine‚ that action is jailed entirely within the container where it can affect only the shadow resources provided in the virtualization layers (OS and CPU) and not those of the native machine. This prevents the unknown file from infecting the endpoint when it executes.
- Two layers of virtualization for better protection: the OS and CPU (when supported)
- Prevents infection across the network from Web, email, documents, USBs and any executable files
- Containment defeats unknown malware from viruses, trojans, and ransomware to zero-day malware and advanced persistent threats on patched or unpatched machines
- Auto-containment of fileless malware to protect system memory with granular security for command line parsers or executors (Windows commands, Python and PERL scripts)
- Extremely lightweight with no performance hits requiring less than 1% CPU and only 20 MG resource usage
- Transparent to end users with no impact on usability; they can run unknown files safely in containment so it is business as usual
- 100% compatible with old or new CPUs whether the user is on or off the corporate network
- Broad OS support including Microsoft Windows, Linux and Mac OS
Related Sources: