Ransomware definition
Updated on October 20, 2022, by Xcitium
Ransomware attacks is a specific type of computer malware that encrypts a victim’s files or systems to prevent them from accessing those files. Consequently, the ransom attacker demands some payment – ransom – from the victim to allow re-access to the files or system. This malware limits users from accessing their data by completely locking the computer’s screen or by restricting access to specific target files in their computers.
Victims of who faced ransomware attacks are provided with a step-by-step guide on how to obtain a decryption key. In recent years, ransomware attackers have shifted to payments made via cryptocurrencies to eliminate the possibility of a trace. Ransom payments range from a few hundred dollars to millions of dollars. In 2017, the most significant who ransomware attacks demand was made to a Korean web hosting company (Internet Nayana). The company ended up parting with $1.14million in ransom payment.
Table of Content
- What is ransomware? and how to prevent from it
- How does Ransomware work?
- Ransomware Infection and Behavior
- Who is the target of ransomware?
- Ransomware facts
- History of Ransomware
- Do you pay a ransom?
- Ransomware Types
- The origins of ransomware
- Mobile Ransomware
- Mac ransomware
- What to do if I’m infected?
- How to prevent ransomware?
- How does ransomware affect your business?
- Ransomware statistics
- List of Top Ransomware till today
- Future trends of ransomware
- What is ransomware-as-a-service (RaaS)?
- Why is it so hard to find ransomware criminals?
- How to defend against ransomware?
- Steps to respond to a ransomware attack
- Ransomware removal
- Ransomware Defense, Prevention, and Removal
- Ransomware news and quick overview
- Conclusion
-
What is ransomware? and how to prevent from it
Serious attention has been given to who faced ransomware attacks for a long time now. You probably have come across an antivirus popup that warns you about some who faced ransomware attacks infection or heard about it at the office. The attention paid to who faced ransomware attacks is not baseless since it poses a legitimate threat to companies’ normal processes of operation. This article aims at providing you with detailed information about everything ransomware.
This article is organized into parts; feel free to navigate to the specific sections that answer your question.
-
How does Ransomware work?
Several types of ransomware attacks exist. Most of them have the same target; that is to take administrative control of systems and files and ask for ransom. However, there is a significant difference in how these who faced ransomware attacks are carried out. The engineering tactics around each attack are often unique, and this is meant to keep victims and other security developers continuously guessing.
Let’s discuss some of the techniques used, to get a deeper understanding of how ransomware attacks works. This section is suitable for both technical and non-technical readers. We shall discuss how some of the most prevalent ransomware, like Apocalypse, Jigsaw, CTB_Locker, Cerber, Unlock92, CyptoWall, Locky, Petya, TeslaCrypt, and TorrentLocker work.
-
Apocalypse Ransomware
Apocalypse was discovered back in 2016, and security experts quickly responded to it before it could widely spread. Apocalypse is unique in that it used an altogether custom encryption pattern or algorithm instead of using the standard algorithms of encryption.
The encryption process of apocalypse is custom-designed, and the encryption key is saved inside a register. After successful encryption, a “dot extension” is added to the file name. Similarly, file decryption procedure is based on an algorithm from the symmetric-key algorithm class- making it relatively easy to decrypt infected files.
-
Jigsaw ransomware
The jigsaw was released in 2016 and has seen subsequent version releases. This ransomware runs in a .net Framework. A “. fun” extension is appended to files encrypted using Jigsaw. It was, however, quickly thrashed by security experts. Arguably, the jigsaw ransomware has the most straightforward approach of all in this list. It primarily employs the AES algorithm in the encryption procedure.
The decryption process is likewise apparent. All you need to do is perform decryption on the encrypted files using the AES algorithm utilizing the exact key and iv.
-
CTB Locker ransomware
It is a relatively old one but made a significant spread in 2014. It uses a more superior encryption algorithm to RSA, and encrypted file names have a 7-character extension that is randomly generated. CTB Locker’s approach to encryption employs both ECDH and AES algorithms. ECDH algorithm leverages an anonymous key agreement protocol and should not be mistaken as an algorithm of encryption. CTB_Locker encryption procedure also uses three encoding levels using ECDH keys that are randomly generated. It uses the key to encode an AES randomly generated key and finally encrypts the target files using the AES algorithm of encryption.
The decryption procedure of files encrypted by this ransomware is simple and straightforward. Since it is impossible to obtain the private ECDH key that corresponds to the available public ECDH key, we only left with two procedural steps. You get a private and randomly generated ECDH key from the C&C server and use it to decode the AES key and then use the AES key to decrypt the encrypted victim files.
-
Cerber ransomware
Cerber was also released in 2016, with the second version of it detected in 2019. The initial Cerber encrypts a victim’s files and adds a “dot Cerber” extension to the file names. It uses RSA and RC4 encryption algorithms. Cerber works in a fairly sophisticated way; it employs three-different levels of encryption juggling between RC4 and RSA encryption algorithms alongside randomly generated keys.
However, a noticeable feature of how Cerber works is that it only affects parts of a file and not the entire file. Decrypting Cerber infected files is easy when you have access to the RSA keys that were randomly generated. These can be obtained from the C&C server. Once you have the key, decryption is done by merely reversing the encryption process. This is done by decrypting the randomly generated RSA key and then decrypting the randomly generated RC4 key. Eventually, use the RC4 to decrypt the file.
-
Unlock92 ransomware
This ransomware was initially released in June 2016 with subsequent versions following through to date. It operates in the .net framework and leaves “a dot CRRRT or a dot CCCRRRPPP” extension to the file name, dependent on the version of Unlock92 used.
In its encryption process, it utilizes the RSA encryption algorithm twice. Each of its samples has a prebuilt RSA key that is usually encoded by base64. Base64 is used to encrypt RSA keys that are randomly generated, which are then used to encrypt target files.
Unlock92 does not encrypt entire files; instead, it only encrypts the initial 0x300 bytes of a file.
The decryption of files involves the restoration of the RSA private key from the C&C server and using the RSA algorithm to decrypt the encrypted files.
-
CryptoWall ransomware
CryptoWall was first detected in 2014, and it has released four different versions to date. CryptoWall uses both the AES encryption algorithm and the RSA encryption algorithm. This type of ransomware primarily targets windows based operating systems. This is because the implementation of encryption algorithms involved is directly dependent on an API called CryptoAPI, which is usually part of Windows-based Operating systems.
When decrypting CryptoWall, you need to go to the C&C server to obtain the RSA private key and then decrypt the AES key that was randomly generated. By the use of that AES key, you decrypt the personal files.
-
Locky ransomware
Locky uses both AES and RSA algorithms in its process of encryption, although different versions offer completely different implementation procedures of the algorithms. In one of its ransomware versions, the AES key generated is initially encrypted by the RSA algorithm, the RSA public key used is obtained from the C&C server. The generated AES key is then used to encrypt files.
Decrypting Locky encrypted files takes after decrypting files that are encrypted by CryptoWall. By utilizing the private RSA key to decrypt the AES key and at last decoding the encrypted data using the same AES key.
-
Petya ransomware
Petya was discovered in March 2016. It makes another uniquely engineered ransomware on this list. It works very differently from the other ransomware on this list. Petya aims to encrypt the NTFS master file table and not personal files as you would expect. Typically, it interferes with the traditional initialization of Windows OS by overriding the bootstrap code in Master Boot Record.
In its encryption procedure, it uses both the ECDH algorithm and the SALSA20 algorithm. Petya uses the ECDH algorithm to encode a randomly generated SALSA20 key. It is important to note that SALSA20 runs in a 16-bit environment and is launched after the ECDH algorithm encodes the randomly generated SALSA key.
The decryption process is equally straightforward in Petya. By only fetching the key for the C & C server, you restore the MBR and MTF respectively by decrypting them using SALSA20.
-
TeslaCrypt ransomware
TeslaCrypt surfaced back in 2015 and has continued to release more versions. It also uses a wide variety of algorithms in each of its releases. In its fourth version, the ransomware utilized ECDH and AES algorithms in its encryption process. It has a close resemblance to CTB_Locker discussed earlier.
TeslaCrypt’s decryption procedure also aligns with the CTB_Locker. You get a private and randomly generated ECDH key from the C&C server and use it to decode the AES key and then use the AES key to decrypt the encrypted victim files.
- TorrentLocker ransomwareTorrentLocker was released in 2014, and it has continued to terrorize the market with newer version releases. Typically, this ransomware appends a “dot encrypted” extension to the name of the encrypted file. TorrentLocker uses a combination of RSA and AES encryption algorithms in its encryption procedure. Most ransomware employs an RSA-AES pattern.A significant difference with TorrentLocker is that here, the AES key is generated by Yarrow Algorithm. Yarrow algorithm seed gives the return value of a diverse function and consequently encrypts the target files in 16 by 16 bytes using the generated AES algorithm.When decrypting, you have to obtain the private RSA key for the server and use AES to decrypt the encrypted files.
-
-
Ransomware Infection and Behavior
Ransomware attacks infections occur in several ways. For standard ransomware attacks, infection is usually the first step. A complete cycle of a ransomware attacks involves Infection, Securing Key Exchange, Encryption, Extortion, and finally Decryption. This chronological order describes the whole behavior of those who faced ransomware attacks.
The infection arrange entails a lot of other factors. For instance, how the ransomware files get to your system. There are four common ways in which ransomware spreads to different clients. A good understanding of these techniques regularly helps internet users in avoiding laid ransomware traps and staying secure.
Here are some of the popular infection routes.
-
Phishing Emails
Emails have become the most common method of spreading ransomware. Phishing emails are designed to lure target users to visit a link or click on an attachment that has a malicious file. These attachments could either be a ZIP file, a Word document, a PDF file, or even a JavaScript file. The ransomware attacks are designed to trick victims into “Enabling Macros,” which then allows them to download malicious “.exe” files by running scripts in the background.
The executable files harbor methods and functions that encrypt specific data or system parts. Ransomware has become extremely advanced and can spread to other systems via a network. This makes it incredibly important for organizations to be on the watch out since a single infection could cripple an entire organization’s network of computers. Ransomware like Locky and Cerber are popularly known to use email phishing as a way of exploiting target victims.
-
Drive-By Downloads
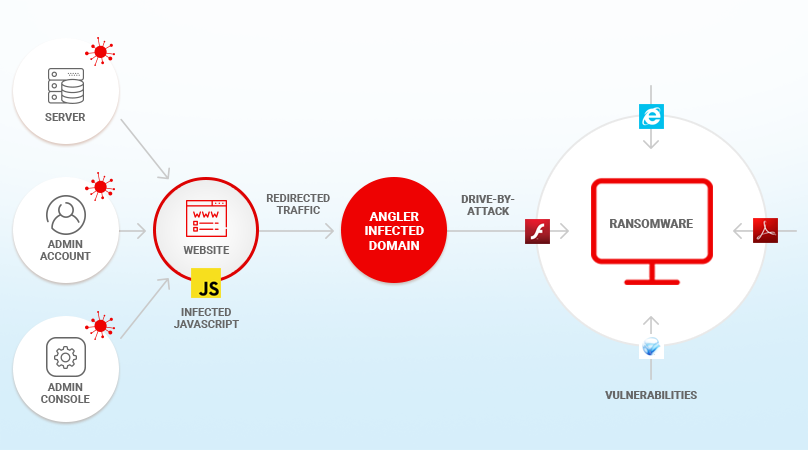
These are malicious downloads that occur behind the scenes – without the knowledge of the victim when visiting a compromised website. This attacking path is dangerous since it doesn’t require much action from the users, making it extremely difficult to protect yourself from this kind of infection. Ransomware attackers then exploit website vulnerabilities by embedding the malware on the target websites. Sometimes they provide auto-redirect links to a vulnerable site where they can then use exploit kits to give them backdoor access to victims.
Drive-By downloads attacks don’t only occur on small, obscure websites; they have also been encountered on popular global sites like The New York Times, the NFL, and the BBC. They were all victims of a ransomware campaign that was conducted through hijacked adverts.
CryptoWall is an excellent example of ransom malware that uses this method of infection.
-
USB and other removable media
The popularity of ransomware continues to increase, and the ransomware attackers are taking every advantage of it. USB devices and other removable media are another common way ransomware experts have used to infect systems and machines. A famous ransom attack was spread to Australians in 2016 using flash disks disguised as a Netflix application on promotion. The external drives infected computers with ransomware. The ransomware could replicate itself to affect other machines connected to the removable drive.
-
Remote Desktop protocol
Ransomware attackers have perfected the art of using the Remote Desktop Approach (RDP) to target victim computers. Typically, this involves controlling other machines in a network remotely, from another administrator computer. The RDP was initially designed to allow IT experts and administrators to configure corporate computers remotely.
This feature offers attackers a chance to exploit the opportunity for malicious acts. Using specialized search engines on the internet like Shodan.io, hackers search and target these computers running with open port 3389 and launch attacks. The most common way these attackers gain access to administrative rights is by Brute-Force-password cracking technique that involves attempting multiple passwords within a short time. This is done with the help of specialized password cracking software and tools such as John the Ripper, Cain and Abel, and Medusa, among others.
Once they gain access to administrative features, they deploy ransomware and disable security features forcing organizations to pay up to re-access their data. Other ransomware that have used this mechanism before are CrySis and LowLevel04.
-
-
Who is the target of ransomware?
In the initial stages of introduction, ransomware mainly targeted individual PCs. Attackers often launched ransomware intending to cripple select PCs and later prompt them to make payment in exchange for their data. However, over time this trend has shifted, focusing on large corporations and Small and Medium Businesses. Ransomware developers realized the enormous opportunity that lies around targeting businesses and companies rather than individuals.
Targeting businesses offers them a chance to charge more since companies rely on their systems to conduct activities. A restriction to their systems severely cripples these organizations forcing them to pay massive amounts of ransom to attackers for them to resume business.
According to a study, about 13 percent of worldwide enterprise detections were ransomware attacks. Similarly, about 35 percent of all SMBs had been faced with ransomware attacks. In the same year, 22 percent of organizations were forced to cease business operations due to attacks. A whopping 81 percent of all businesses had experienced one or multiple cyberattacks. The statistics are endless, and they all show that corporates and small & medium enterprises are more vulnerable to ransomware attacks than the average internet user.
Geographically, ransomware attacks seem to be most prevalent in the East and Western countries. Organizations in countries like Saudi Arabia, Turkey, China, Spain, United Kingdom, United States, and Mexico recorded the highest number of ransom attacks. Surprisingly, in South Africa, about 60% of organizations also reported some form of a ransomware attack.
-
Ransomware facts
Cybercrime has continued to evolve, changing infection strategies, encryption procedures as well as target areas of encryption. Here are some of the facts about ransomware in the previous years.
- In the US, about 66 percent of ransomware attacks in 2019 target local and state governments.
- Towards the end of 2019, the average ransomware payout rose to $41,000
- More than 500 Academic Institutions experienced a ransomware attack in 2019
- About half of small and medium-sized businesses are willing to pay hackers a fee to regain access to their data.
- Nearly 150 Local governments, medical institutions, and police stations recorded a ransomware infection in 2019
Let’s look at some of the outstanding ransomware attacks that demanded successful or unsuccessful payouts in 2019.
- Surprisingly, in South Africa, about 60% of organizations also reported some form of were faced ransomware attacks. This attack crippled the health center for two consecutive months, locking them out of their system. The facility had to operate on a manual paper and file system for seven weeks without the ability to make schedules and appointments. The health facility ended up paying $70,000 in ransom.
- An urban town in Ontario, Canada, who faced ransomware attacks by deploying malware that encrypted their servers and completely locked them out of data. The city had to pay a ransom worth 10 BTC, which converted to about $71000.
- Similarly, in June 2019, the county of La Porte in Indiana was attacked by ransomware. Luckily, the IT experts realized the spread of the malware and managed to contain it to a small portion of the network. The FBI attempted, in conjunction with a forensic investigation firm, to recover the data, forcing the county to pay $130,000 in ransom. Insurance covered about $100,000 of this amount.
- Jackson County in Georgia comes in fourth. This attack was made in March 2019, where Jackson County faced a terrible shutdown of all its services. The Ransomware only spared its police emergency system (911) and the county’s website. This ransomware was later discovered to be a Ryuk ransomware strain, which was a nightmare for many schools in 2019 as well as affecting more than 500 Schools. The county had to pay a ransom of $400000 in payment to regain access to their system.
- In Florida, The Lake City was also crippled by a ransomware attack in June 2019. This attack spread so fast, managing to paralyze most of their systems. This brought about operational issues in the city. This attack restricted access to city council agendas, resolutions, ordinances, meeting minutes, among others. After a few weeks, the Lake City, through its insurance, paid $500000 worth of ransom to recover some of their data. Not all the data was recovered due to delayed agreements. This was another Ryuk ransomware.
- We close the list with Riviera Beach City, again in Florida. This attack took place in May 2019, and it demanded the highest ransom payout in 2019. According to reports, a City employee fell into the trap of a phishing email, and the attackers immediately gained access to the entire City’s system. This affected payment procedures, communication routes, and even utility pumps. The city officials agreed to pay $600000 as requested by the attacker, using about $300000 from their Insurance Policy. Sadly, this attack happened shortly after Riviera Beach City invested about $1 million to replace its computer equipment.
Ransomware Infects Critical Files
As earlier mentioned, the ransomware industry is continually evolving and adopting new security barriers developed. In this section, we will discuss a bit about critical files, how ransomware targets them, and why they are a priority target for ransomware attacks.
A critical file is an essential file in a system that is necessary for the operating system to operate smoothly. Ransomware that affects the critical files often depends on patched malware to infect systems successfully.
Patched malware is a file – a legitimate file – that has undergone modifications caused by malicious code. Ransomware cyber attackers prey on these files to infect systems since they are used quite often when the system is running. This explains why cyber attackers target such files, since the higher the number of times a file is executed, the higher the rate of execution of the embedded malicious code.
For instance, a popular police ransomware targets and infects the user32.DLL – which is a well-known critical file. This technique makes it extremely difficult for security tools to detect malicious activities. Launching attacks at critical files have a couple of advantages, such as acting as an evasion technique from security tools that monitor system behavior.
Cleaning critical files requires extreme care; for this reason, cleaning tools often don’t touch them making it a relatively safe area of residence to malicious codes.
The infected user32.DLL file then acts in its own capacity, and eventually loads the actual ransomware to the system. At this point, the ransomware locks the screen and displays a ransom message.
-
History of Ransomware
Ransomware only managed to become a global threat in the mid-2000s; the first attacks of this manner happened much earlier. The first-ever recorded ransomware attack occurred in 1989, and it targeted a healthcare facility. In 1989, an AIDS researcher, Dr. Joseph Popp infected floppy disks with malware and later distributed around 20000 copies of the floppy disks to other international researchers in 90 countries.
According to the report, Dr. Popp claimed that the drives contained a useful computer-based program that could assess the risks of contracting AIDs based on a questionnaire. This ransomware, however, infected the computers and later on demanded a ransom payment. The malware remained dormant in the infected computers for days, and it only got activated after the machine was rebooted 90 times. After this threshold, the ransomware executed itself and displayed a ransom message on the screen, demanding payment to regain access. According to the report, the ransom payment requested was between $189 and $378.
This attack later was called the AIDS virus of the digital world or PC Cyborg. However, the ransomware was poorly engineered and contained a wide range of vulnerabilities. But it set the base for subsequent ransomware that became more sophisticated in their approach. Subsequent ransomware creators usually wrote their custom encryption codes and algorithms.

A few other ransomware attacks popped up after that; however, the next noticeable threat was witnessed in 2014 when relatively weak RSA codes were used by GpCode to encrypt personal files for ransom. Three years later, in 2017, WinLock ransomware surfaced and changed the game a little bit. WinLock shifted away from the usual ransomware target, by opting to lock users out of their system and displaying adult content images on the screen and asking for ransom via SMS.
Years later, after the WinLock nightmare came the Reveton family in 2012. This type of ransomware also took a unique approach. It took over victims’ computers and masqueraded as police departments and other law enforcement agencies. It would display an impressive background of these legitimate agencies and then claim that the hacked victim had committed a crime. They then asked for ransom, which reportedly ranged from $100 to $3000 paid via prepaid cards.
This technique was successful because of the social engineering involved; most victims preferred paying the ransom rather than being associated with dreaded criminal activities such as child pornography, although they were innocent.
As of 2013, a different breed of ransomware began to pop up. CrytpoLocker introduced another version that was far more complex using military encryption. It employed a different approach that involved the use of a decryption key that resided on a server. You had to use that key to decrypt encrypted files. As a result of this practical approach, several other ransomware adopted the same trend. Petya and WannaCry used the same technique. Around this time, numerous attacks emerged, targeting both private and government facilities.
Ryuk came into the scene in 2018 and terrorized several government and news publications in the US. Ryuk is extraordinarily efficient and sophisticated. Ryuk was used to infect some city-systems in Florida, amongst other targets. And in 2019, the ransomware known as Sodinokibi was detected, which reportedly made attacks as well.
Over time, developers began to shift to pre-developed encryption algorithms that are offered as off the shelf libraries. These libraries are carefully developed and contain very sophisticated algorithms that are often difficult to crack. Additionally, ransomware attacks have evolved into advanced and high-level infection methods. Most ransomware do not require physical devices like floppy disks, as in the case of Joseph Popp. Today’s ransomware attacks are launched via advanced techniques such as spear-phishing campaigns as opposed to traditional phishing emails that most spam filters managed to fight.
-
Do you pay a ransom?
At this point, it is clear that ransomware is a global problem that has the potential of attacking and crippling nearly any digital entity. For this reason, it is prudent to understand whether or not it is advisable to pay a ransom when you face an attack.
This is a topic that has had its fair share of debate. With the current level of ransomware sophistication in the digital world, it has become a significant challenge for security experts and even FBI to crack these encryptions leaving victims of the attacks at serious crossroads. Often when faced by an attack, particularly for corporations, and governmental institutions, an ultimatum is issued to them for when the payment should be made.
During this time, victims think about options available to them to decrypt their files without succumbing to the demands of the hackers. Most of the time, not paying the ransom has proven not to be a good option for victims who are not ready to lose their data. Studies show that about 70% of small and medium-sized businesses that have experienced ransomware attacks have ended up paying.
Assuming that you are already attacked, the decision you’ll make is entirely relative to what you stand to lose. In the case of a personal computer, you may consider not paying up the ransom requested and opt to replace your machine if there is no sensitive data on your device that you would mind losing.
However, businesses risk losing client data, financial records, and appointments if they refuse to pay up, a quick cost-benefit analysis can be done to determine what option is best. Looking at the trends in previous ransomware payment demands, it’s clear that most would prefer to pay up and regain operations as they work on adjusting security features against future attacks.
Disclaimer: Although most ransomware attackers offer solutions after pay, these are criminals who enjoy preying on people’s vulnerabilities, and therefore, a solution to your problem is not always guaranteed.
-
Ransomware Types
Ransomware can be classified into three main categories considering severity levels. Below is a breakdown of the three types of ransomware;
-
Scareware
Scareware is a unique type of malware that uses social engineering tactics to get users into performing a particular task. Typically, this type of malware is initiated by a computer pop up or an advert. For instance, PC users are always on the lookout for potential virus threats. Scareware masquerading as an antivirus pop could easily trick such users into clicking it and installing a “fake” antivirus. By downloading and installing these infected files, users find themselves with ransomware instead.
An excellent example of a scareware scheme happened in 2010 when Ads were popping up on the Minneapolis Star Tribune that redirected them to malicious sites. These users became victims of a malicious Windows advertising campaign that prompted users to purchase an antivirus for $49.95. Eight years later, a Latvian national was later arrested for being behind the scareware attack.
-
Screen Lockers
A step higher from scareware are the screen lockers. This type of ransomware is rigorous in its attack process. When a screen locker infects a system, the victim is entirely restricted from accessing their PC. An example of such ransomware is the WinLock. A full-screen message is displayed upon booting. They often demand pay claiming the victim has committed some unlawful activity.
-
Encrypting Ransomware
Encrypting ransomware is far more complicated compared to screen lockers and scareware. These types of malware target personal files and encrypt them using complex algorithms. It has been a challenge to counter these kinds of attacks since decrypting already encrypted files without the help of the attackers is almost impossible. For this reason, many ransomware attacks have been launched over the years using this strategy.
Once your files are encrypted, the only logical way to decrypt and regain access is by paying the demanded ransom. Unfortunately, paying the ransom to hackers does not offer you a total guarantee that your files will be decrypted. It is always a gamble. An example of this type of ransomware is CryptoLocker.
The Evolution to CryptoLocker and Crypto-ransomware
CrytpoLocker emerged in 2013 and introduced a new approach. At this time, screen lockers were very popular. CrytpoLocker infected personal computers with or without antivirus protection and encrypted personal files restricting access. The developers made sure that the ransomware could encrypt files even with the presence of an antivirus. Although some antivirus software was able to detect and delete it, CrytpoLocker ensured that it compelled its victims to pay the ransom even after it was deleted. When the payment is made, a decrypt key is availed to the victim to enable them to decrypt their files.
According to security analysts, CrytpoLocker uses both AES and RSA encryption, however on their note, only RSA-2048 is listed. An apparent difference between RSA and AES is that AES utilizes symmetric keys; this means that one key used to encrypt is the same as the one required to decrypt. As for RSA- which is asymmetric key cryptography, a public key is used to encrypt the target file and is made available to anyone. However, it keeps a private key that is required to decrypt the encrypted data.
In this case, the ransomware is engineered first to use the AES key to encrypt the target file. The AES requires the same key for decryption; hence the key is written in the encrypted data. Next, an RSA public key is used to encrypt the AES key. So, to successfully decrypt these files, a private RSA key will be needed.
Towards the end of 2013, a different kind of CryptoLocker was detected. This particular variant of CryptoLocker can spread through secondary drives. This was an unusual feature for CRILOCK variants. This feature made this variant more dangerous since it could spread much faster than the others. Some researchers believe that this CryptoLocker was the work of a copycat.
Not so long after, Cryptorbit surfaced. Cryptorbit was also known as the Crypto-ransomware or CryptoDefense. This encrypting ransomware targeted databases, scripts, web videos, text, images, and several other file types. It also deleted backup files to avoid restoration attempts and finally asked for a ransom payment in exchange for a decrypt key.
-
-
The origins of ransomware
AIDS by Joseph Popp was the first-ever documented malware attack in the history of ransomware. This happened in 1989, and it had severe malfunctions that made it ridiculously insane even to consider paying the ransom to the extortionist. AIDS Trojan – which was its other name, apparently encrypted file names and not the files itself?
Joseph Popp was later on arrested, but unfortunately, he was declared mentally unfit to face trial for his actions. However, he pledged to fund AIDS research with the profits he made from the ransomware.
-
Mobile Ransomware
This is a special kind of ransomware that attacks mobile devices. This type of ransomware has the same goal as on PCs; they aim at extorting the victim by denying them access to their data or peddling false criminal accusations. Typical mobile ransomware attacks would either lock users from accessing their devices or steal sensitive information from mobile devices and ask for ransom for restoration.
Alternatively, mobile ransomware attacks victims can also be threatened by fake accusations of unlawful behavior, prompting them to pay the ransom. Today, most extortionists prefer bitcoin and other cryptocurrencies as a mode of payment due to the inability to trace transactions to them.
Two recent mobile ransomware are CryptoLocker and DoubleLocker. CrytpoLocker infected several mobile phones, both Android and Apple phones. In the same year, DoubleLocker – which is Android ransomware, infected several smartphones as well. The DoubleLocker spread through vulnerable websites that hosted fake mobile apps. This mobile ransomware messed with the phone’s pin and consequently encrypted the original files of storage. They demanded a ransom for this to be uplifted or decrypted.
There is Koler malware. This mobile ransomware masquerades as an adult-themed app infecting mobile phones in the US. It typically displays a screen with adult-related content and asks the user for ransom. The ransom malware, once downloaded, gains administrative access to the device, giving attackers full control upon installation.
-
Mac ransomware
Mac users used to pride themselves as immune to cyber-attacks since a majority of attackers targeted Windows PC users. This trend has changed over time, and now Mac users also face a fair share of cybersecurity issues.
It is, however, true that Windows users are more vulnerable to attacks compared to Mac users. This is a hot topic in the IT field; it is argued that many people use Windows OS; therefore, attackers tend to focus on the majority to maximize their reach.
Mac ransomware exists and has been on the rise, according to this report, the ransomware targeting Mac computers increased by a whopping 60% in the last three months of 2018. Mac computer users have experienced a relatively low number of ransomware attacks. Below are some of the known Mac ransomware;
In February 2017, a Mac ransomware, known as Filezip or Patcher, managed to infiltrate and terrorize some Mac users. The ransomware encrypted the user’s files and asked for 0.25Bitcoin in ransom for decryption. Unfortunately, these attackers were not able to decrypt the data as well; therefore, paying the ransom was meaningless.
Another Mac ransomware of concern surfaced in 2016; it infiltrated Mac machines from a BitTorrent Client update that saw where it was embedded with an authorized security certificate. This enabled it to bypass the macOS gatekeeper. KeRanger demanded a ransom of 1 Bitcoin upon infection and is reportedly still under development.
In 2014, FileCoder spread among Mac computers; however, it was relatively harmless. FileCoder never encrypted users’ files; instead, it displayed a window on the screen, demanding ransom.
In 2013 Mac Safari browser was also targeted by ransomware. It was known as the FBI/MoneyPak Scam. This Mac ransomware demanded a $300 payment from victims to regain access. The ransomware relaunched automatically whenever safari was launched in case the user force quit the safari browser.
Although Mac users do not face imminent risks of ransomware attacks compared to windows, interest has begun to rise, and many hackers are taking an interest in the platform. Mac users should just be on the lookout for ransomware traps, just like Windows users should.
-
What to do if I’m infected
According to the FBI, when ransomware attacks your computer, you should commit to not yielding to the demands by not paying the ransom. The argument is, the more we pay ransom payments to these extortionists, and the more we encourage the industry. Although the FBI hasn’t been able to find decrypting solutions to all the ransomware, some solutions already exist that allow victims to at least retrieve a good chunk of their encrypted data.
Historically, most attempts to decrypt files without the help of the ransomware attackers have failed and lead to nothing but further encryption. For this reason, victims should not attempt to decrypt important files without consulting experts, as this could lead to permanent loss of data.
When you are already infected by ransomware, you should delete or remove the malware to thwart the chances of further damage. To remove the threat, you should download a remediation-which is a security product that runs on your machine and scans it for potential malware threats. If it finds the malware, it will delete it to eliminate the risk. This is a procedure used to clean up your PC post damage; however, it is not a solution that helps you regain access to your encrypted files. If, for example, you have a screen locker ransomware, a complete boot-up process is necessary using external bootable devices like USB drives.
Sometimes, your machine can be under attack right in front of you. When you notice unnecessary lags from your computer without any apparent reason, or you suspect you are under an attack, you should disconnect from the internet and switch off your machine. This prevents the ransomware from successfully installing to your system since most of them require instructional codes from a remote server that are executed behind the scenes. So when you prevent this from happening, you can restart your computer and run security products for remediation and clean your system.
Although you shouldn’t pay the ransom, sometimes conventions are not the best solutions. There is a reason behind every significant payment ever made. An analysis should be done to determine the impacts of losing the data against the cost of paying the ransom.
-
How to prevent ransomware?
All ransomware attacks often take advantage of a security loophole in the system. A few ground rules are there to help sensitize the public with preventive measures against these nefarious who faced ransomware attacks. Here a few general tips regarding precautionary measures.
Do not visit unknown or unverified links. Links are an accessible mode of peddling ransomware among attackers. It is safe to avoid clicking on unfamiliar links from adverts or unsolicited emails. Most ransomware is downloaded by clicking unknown links that consequently initiate downloads. Victims often do not realize they are infected until the ransomware completely takes over control.
Never download/open unknown or untrusted email attachments.Phishing emails are a standard route for ransomware perpetrators. Often when you receive an email from unknown sources, you should not be quick to open associated attachments. If you are doubtful about the email, refrain from opening the attachments and confirm with the sender. If you come across an email attachment that requires you to enable macros, do not enable. Enabling macros allows the malicious code to take over your computer and lock you out.
Download files from trusted websites onlyYou should be very careful in choosing the websites from which you can download files. Popular and verified sites have a better chance of protecting their data from ransomware, which in turn makes it safer for you. The SSL certificate on a website has been a standard mark of trust for most sites today. All well-known and trusted sites are prefixed with “https” instead of the regular “Http” which is prone to security breaches.
Do not give out personal information.Attackers sometimes go as far as making phone calls or sending text messages in an attempt to gain access to personal information beforehand. They use this information to craft personalized emails that target victims with their personal data, making phishing emails looks more legitimate. When you receive an anonymous call asking for personal data, you should always say no.
Utilize email filtering and scanning featuresEmail servers have content and file scanners and filtering features. Using these features on your emails dramatically reduces your chance of getting into a ransomware trap. Filtering and scanning scrutinizes your emails and sends suspicious emails to the spam folder.
Do not accept unsolicited USBsUnknown devices are generally not supposed to be used on your computer. Cyber attackers sometimes leave infected USBs in public places hoping that someone would fall victim. It’s, therefore, an excellent preventive measure to avoid sticking unknown USB drives on your computer.
On a Public Wi-Fi, always use a VPNPublic Wi-Fi poses a considerable security threat to its users. Attackers connected to the same Wi-Fi can infiltrate your device. To stay safe, additional security measures should be employed. The use of a secure Virtual Private Network (VPN) can help in reducing the chances of a successful attack.
Always update your operating system and software.Operating systems, software, mobile applications, and browsers are regularly being updated. In most of their changelogs, security updates are a common occurrence. Security updates are made to offer the highest possible protection from potential attacks and correct detected areas of vulnerabilities.
Use Security SoftwareUsing security software can go a long way in preventing ransomware attacks. Ransomware protection is becoming more crucial, and companies like Kaspersky are offering decent protection against potential ransomware attacks.
Backup your important dataBacking up important data is not a preventive strategy but a precautionary act. In the event of a ransomware attack, you’ll have access to you’re backed up data. When backing up, it is advisable to use external devices and keep the devices disconnected from the computers in a network to avoid infection.
-
How does ransomware affect your business?
A good understanding of how ransomware affects your business can help decision-makers in taking more precautions in their operations. Here are some of the effects;
Prevents you from accessing dataSmall and medium-sized businesses of today heavily rely on data for their day to day operations. Nearly all sectors of business operations have been successfully digitized, making computers and data a significant part of a business. Due to this, restricting access to this information results in severe crippling of companies. Business owners and administrators, therefore, should be vigilant, looking for safer and protective ways to protect themselves from the virus.
Costs of Restoration are high. In the event of a successful ransomware attack, data is always damaged when the ransom is not paid. When a business keeps a backup of their data, depending on the volume, restoration can be costly and time-consuming. Additionally, the magnitude of data loss caused by the ransomware may render data recovery pointless and expensive. This makes external backups the best priority as a precautionary measure for businesses.
Damage of Reputation Client trust is vital for companies, and a tiny taint to a business reputation will impact them negatively. For instance, a company that sells products online via an e-commerce website will lose clients’ trust when their site gets hacked. Customers would not want to make online payments via the site due to fear of ransomware attacks.
Disruption of Normal Business Operations To get a clear picture of how disruption can be disastrous to business, let’s visualize a manufacturing firm. When ransomware successfully hits a manufacturing firm, all data is encrypted and control systems are disabled, and an inevitable downtime will be experienced. The interference faced can cause significant losses in millions of dollars. Similarly, ransomware’s ability to immediately halt vital processes of a business may cause small and medium-sized enterprises to incur severe losses and even shut down.
-
Ransomware statistics
Here are random statistics about ransomware in the past years to date.
Cybersecurity Ventures forecasts that global organizations will spend about $20 Billion on ransomware attacks by 2021. This is a massive rise from previous years. In 2018 and 2019, Cybersecurity Ventures estimated that ransomware costs would be $8 billion and $11.5 billion, respectively.
The Ryuk ransomware alone commanded an average ransomware amount of $377,000 in the third quarter of 2019
In 2019, the costs of ransomware attacks surpassed the $7.5 billion mark. This report focused on attacks launched on government agencies, educational institutions, and healthcare providers.
In the last quarter of 2019, ransom payment amounts saw a significant rise of about 104% in average payments. The average demand rose to $84,116, with the highest reported payment incident of $780,000.
The healthcare sector in the US has faced numerous and severe ransomware attacks. According to the research, 172 different ransomware attacks made targeted clinics, healthcare organizations, and hospitals. All these attacks range from 2016 with an estimated cost of $157 million.
In 2019 an inexorable rise in ransomware attacks happened. Ryuk, as a single ransomware, recorded an increase of 543% during the last three months of 2018. Again, Sodinokibi ransomware- which was introduced in May 2019, recorded a rise of 820% in the number of detections.
According to Kaspersky Lab reports, mobile ransomware installations increased in 2019 from 8,186 in 2018 to 68,000. This showed a significant increase in ransomware Trojans; however, ransomware cases decreased gradually throughout the 2019 quarters with quarter one recording the highest (27,928) and the last quarter recording the lowest (3,951).
Over 1000 different US organizations experienced some form of ransomware attacks in 2019
36% of ransomware attacks aim to disrupt normal business operations
A total of 6.6 million patients have been affected by ransomware attacks on healthcare facilities since 2016
Municipalities experienced an increase of 60% in ransomware attacks in 2019
More than half of all ransomware target schools and educational institutions. The figure is placed at 61%.
Small and Medium-sized businesses make up 20% of the victims of who faced ransomware attacks.
In the corporate world, about 645 employees were victims of a who faced ransomware attacks in the third quarter of 2019.
-
List of Top Ransomware till today
There have been several cases of reported ransomware incidents over the years. Here we will discuss some of the most notorious ransomware in history to date.
- Bad Rabbit Bad Rabbit ransomware became prevalent in Russia and other parts of Eastern Europe. It is closely similar and related to the malicious strain of code that was associated with WannaCry and NotPetya ransomware. Bad Rabbit masqueraded itself as an Adobe Flash Installer. It primarily spread through drive-by downloads from untrusted websites. When the victims clicked on the malicious Adobe installer, the computer automatically went off. Bad Rabbit commonly demanded $280 in ransom with a deadline of 40 hours.
- Cerber This ransomware attack was relatively evolved. Cerber was primarily distributed as RaaS- also known as Ransomware as a service through an affiliate program. It offered a unique business model where any interested party could download and use it, in exchange for 40 percent of the profits made. Cerber mainly targeted those who used Office 365 through a sophisticated phishing campaign. Once clicked, it would run in the backend without any indication until encryption was complete. In 2017, when Cerber was at its peak of infection, it was responsible for 26 percent who faced ransomware attacks. Cerber uses the RSA encryption algorithm; to date, there are no reliable free decrypting solutions in the market.
- Dharma Dharma was first detected in 2016 and has since then released new versions of the ransomware. It mainly uses the AES 256 encryption algorithm to encrypt files. It notably deleted the shadow copies of the encrypted files as well. Dharma is classified as a cryptovirus, and it mainly exploits email vulnerabilities. The ransom malware appends different file extension names to encrypted files such as “USA”, “.xwx”, “.dharma”, “.best” and “.gif” among othersCurrently, Kaspersky Lab has a decryption tool that can decrypt files with the “. dharma” extension.
- GandCrab This is regarded as the most popular ransomware of 2018. GandCrab malware targets Windows PCs and is hugely reliant on Windows PowerShell, VBScript, and Microsoft Office macros. It used phishing emails as a route to get to victims by mainly designing consumer-model phishing emails. GandCrab ransom demands ranged anywhere from $500 to $600.GandCrab reportedly attacked more than 48,000 nodes in its first month of release in Jan 2018. A sophisticated team of cybersecurity agencies teamed up and successfully hacked GandCrab servers and released decryption keys for free. The team consisted of Europol, Bitdefender, the Police Department of Romania, and the General Prosecutor’s Office.
- Jigsaw malware used a relatively brutal attack mechanism. It encrypted the user’s files and then went ahead to delete them systematically over time. Jigsaw ransomware demanded $150 worth of ransom within 24 hours, after which the victim’s files would automatically begin to self-delete progressively. Jigsaw deleted even more data if the victim attempted to shut down the computer after infection forcefully.
- Katyusha Katyusha malware was first detected in October 2018 encrypting files and appending a “dot katyusha” extension to encrypted files. It demanded a ransom amount of 0.5 bitcoin with a 72-hour ultimatum. Katyusha ransomware threatens to expose encrypted data to the public if the ransom is not paid.
- WannaCry WannaCry is arguably the most popular ransomware of all time throughout the globe. It is estimated that the ransomware infected close to 125,000 different organizations spread across 150 countries. WannaCry ransom malware is also known as WanaCryptOr or Wcry. It targeted computers running on Windows operating systems and demanded ransom payment in Bitcoin. According to Wikipedia, the WannaCry 2017 attack reportedly originated in North Korea.
- GoldenEye This ransom malware is closely compared to the infamous Petya ransomware. It primarily targeted the Human Resource departments of organizations. GoldenEye spread through an elaborate social engineering campaign on the internet. GoldenEye operated stealthily on computers and launched a macro that encrypted files on the victim’s computer.
- LockerGoda LockerGoda has been seen in action in 2019, paralyzing manufacturing and industrial firms. It is a relatively new type of ransomware with serious complexities surrounding it. It locks victims entirely out of the infected systems. It is also challenging for anti-malware software to detect LockerGoda.
- PewCrypt PewCrypt is yet another 2019 ransomware on the list with entirely different goals. If you have ever been curious about which channel is the most popular on YouTube, then you must have heard of PewDiePie. PewCrypt is ransomware, allegedly developed by fans of the popular PewDiePie channel to get more subscribers to their favorite channel, to hit the 100m subscribers mark ahead of other competitor channels.PewCrypt was mainly distributed through email campaigns and other compromised websites.
- Ryuk Ryuk’s family of ransomware made their debut in August 2018 and has caused massive impacts. Since then, Ryuk has claimed over 52 significant ransom payments totaling to $3.7 million in Bitcoin. Notably, this ransomware targets more prominent clients like businesses and government institutions.
- SamSam This malware also seems to be used only in targeted attacks on Industries, healthcare institutions, and government institutions such as municipalities. For instance, SamSam was used to paralyze the City of Atlanta, which eventually cost the residents about $17 million. SamSam ransomware is one of the few ransomware that uses the Remote Desktop Protocol approach that was discussed earlier.
- Sodinokibi This ransomware attack is also known as REvil. It is a Ransomware-as-a-Service model that was discovered in April 2019. Sodinokibi uses many infection vectors, such as directly exploiting security vulnerabilities and using email phishing campaigns. Sodinokibi can access administrative rights in a machine by exploiting a vulnerability in Oracle WebLogic.In August 2019, Sodinokibi attacked several local governments in Texas and extended its reach to affect remote data backup service that was used by several dental practices in the US. Sodinoki locks users’ files, and decryption requires a key. There are no free tools to decrypt files encrypted by Sodinokibi ransomware.
- Bitpaymer BitPaymer is a ransomware kind of virus. Immediately after infecting, it encrypts most of the frequently used files and adds a “dot locked” extension to the file name; however, the updated version appends a “dot LOCK” extension. BitPaymer is also known as “wp_encrypt”. It is primarily spread by infected email attachments (macros), through compromised and malicious websites as well as torrent websites. BitPaymer is also known as DoppelPaymer.
- Phobos ransomware was introduced in 2017, and it has since been linked to Dharma ransomware. Phobos is distributed through exploiting connections of the Remote Desktop (RDP). The malware continues to encrypt files in the background even after the ransom message pops up. Phobos uses multiple persistence mechanisms such as adding itself in the Startup folder, self-installs in %APPDATA%, and adding commands to the registry keys to initiate it upon system boot-up automatically. As a means to establish trust among their victims, Phobos developers offer free decryption of a few files to prove their ability to decrypt the data. In their ransom demand message, the developers warn against attempting to decrypt data using third party tools-as it could lead to permanent data loss. The ransom prices increase with time, forcing victims to pay up as soon as within six hours of the attack.
-
Future trends of ransomware
Many possibilities are surrounding the tech industry, and ransomware isn’t any different. Although it can be challenging to make accurate predictions involving figures, a few likely trends can be forecasted.
Ransomware attacks are bound to increase in the coming years. This unfortunate trend is almost inevitable since ransomware creators are good at adapting to new technologies and continually developing sophisticated ransomware in return.
There are two main matters of concern, according to the report. Ransomware has evolved in 2019 and 2020 and is currently able to attack virtually any sector, from governments to manufacturing firms to healthcare facilities – the list is endless. There is no one safe from who faced ransomware attacks; again, ransom developers are increasingly adopting a trend of threatening to release critical information to the public upon successful hacks. This leaves high-profile victims with virtually no option but to pay the ransom out of fear of leaking sensitive information.
Here are some of the significant trends to watch out for;
- In the future, courts will be involved in the ransomware landscape, influencing the behavior of both ransomware perpetrators and victims.
- Successfully carrying out ransomware attacks will be more difficult, limiting it to only a small section of highly experienced individuals or groups. Notable trends show that novice cybercriminals will continue to be scammed in the black market with fake products.
- Although the US has accounted for more than half (53 percent) of all who faced ransomware attacks between 2018-2019, the trend is about to shift as cybercriminals start to focus their attention on other countries.
- Finally, the RaaS business will continue to attack the market. Beginner criminals depend on this model as a means to prey on smaller unsuspecting targets. RaaS ads are continuously increasing in the darknet fueling, and the demand is also rising.
-
What is ransomware-as-a-service (RaaS)?
Ransomware-as-a-service is a recent development in the industry that has seen a significant rise in the spread of ransomware. RaaS is cloud-based ransomware sold to distributors at a fee; the distributors then oversee the spread of the virus to the innocent public. The RaaS creators often take a cut from the percentage of profits made from victims.
As you can see, this is a very profitable business model since millions of dollars have been paid as ransom over the last few years. This model has become extremely popular since it allows both skilled and unskilled programmers and computer users to launch ransomware attacks successfully. In the past, this wasn’t possible since launching a who faced ransomware attacks required a considerable level of coding and programming skills.
Before the popularity of RaaS, cybercriminals often hacked and breached data systems. They then had to contact victims and negotiate on a price before they returned the data. This method wasn’t as efficient as ransomware is today. With ransomware, built-in buyers are available, and victims are often required to pay, without negotiation, or lose their data.
-
Why is it so hard to find ransomware criminals?
Advanced cybercriminals are often cautious individuals who know how to cover their tracks. This makes it challenging to trace them. Here are a few reasons why most of these criminals get away with a crime.
It is time-consuming to track careful cybercriminals. Ransomware criminals sometimes use stolen devices and camouflage their tracks through other compromised systems leaving a trail of systems. Again most criminals channel their attacks through multiple systems in different countries that are often inaccessible or not easy to traverse. Ransomware attackers also often involve Tor, which is anonymous and makes it even harder for authorities to track them.
-
How to defend against ransomware?
There are a few proven ways that can help personal computer users; organizations minimize their risk of ransomware infection.
Be extremely cautious when clicking on links in emails or untrusted websites. If you have the time, verify website addresses individually before visiting. Some malicious sites appear to be identical to well-known websites only with slight variations in their domain names.
When you receive an email with attachments from unknown sources, refrain from clicking on the attachments. Phishing emails are a widespread mode of ransomware distribution. Most of the ransomware attachments are in the form of compressed files such as ZIP files.
Always update your machine software to the latest version. Software updates are essential for security reasons. Regularly updating your computer’s operating system reduces the chances of who faced ransomware attacks. This is because Operating System developers are also continually fixing security loopholes in their software to minimize chances of attack.
Keep yourself informed about the latest trends in cybersecurity. Information is power, and it helps you avoid common traps that ransomware attackers have laid for the unsuspecting internet user.
Confirm and verify your emails and senders. Phishing emails are sometimes very smart, and if you are not keen, you may fall into their trap. Emails are often well crafted and sent to targeted recipients.
Use anti-malware software to maintain and prevent your computer from possible attacks. Such software includes email filters, antivirus software, and firewalls, among others.
-
Steps to respond to a ransomware attackS
Once infected, you are faced with a different challenge, and a few steps should be followed. In a typical ransomware attack case, victims are supposed to disconnect the infected machine from any network system available. Victims are advised to disconnect from Wi-Fi, Bluetooth, and any other network connection to avoid the spread of the ransomware.
When disconnected, if possible, you should turn off the infected system. All other computers and devices that share a network with the infected device should also be turned off. These steps may turn out useful to security experts during data recovery attempts. Sometimes, using computers that are halfway encrypted can give insights to experts on how to go about the decryption or data recovery.
Secure your backup files. When faced with an attack and you have some backup data, ensure that the data is safe by disconnecting it from the machine. Preferably secondary storages are suitable for backing up data. If you can, use a different device to scan your backup for any malware.
-
Ransomware removal
There are three types of ransomware attacks, scareware, screen lockers, and data encrypting malware. The severity of this ransomware is different, with scareware being the least dangerous and easy to remove, followed by screen lockers and finally data encrypting ransomware that are incredibly complex.
How to remove ransomware?
The difficulty in removing malware from your computer varies depending on the type of ransomware that infected your computer. Removing scareware and some screen lockers is easy. If you have an antivirus program installed on the machine, a simple scan will most likely detect who faced ransomware attacks and give you options to delete them.
When you have a backup, you can remove ransomware by formatting your infected disk, scanning for existent ransomware, and finally restoring the data from a backup source.
In some cases, decrypting tools can help you remove malware and restore your files. Although this could be a gamble, it is sometimes a valuable procedure. When infected by ransomware attacks, you can look for possible decryption software online. Most malware gets attention because of its popularity and frequency of attacks. As a result, counter organizations and individuals are developing decryption tools that help victims in recovering their encrypted data.
When infected, you can use No More Ransomware Attacks. To identify the type of malware that has infected your PC. This is generally done by uploading the ransomware note, web address, or email.
When they recognize the ransomware, they’ll give you solutions or necessary steps on how to restore your data, whenever possible.
-
Ransomware Defense, Prevention, and Removal
Removal of ransomware attacks varies in difficulty and is highly dependent on the type of ransomware. The most common approaches to ransomware removal involve;
- Wipe and Restore This is the best option for personal computer users and small businesses. If you have an external backup, it is advisable to wipe your computer completely – by formatting to eliminate all the traces of ransomware and then restore the data from a clean backup.
- Decrypt data Decrypting data doesn’t serve the purpose of removing data. However, it helps in the restoration of data by reversing the encryption procedure. This is sometimes a complicated procedure that average computer users may not be able to perform. Again, not all ransomware encrypts data in a way that it can be reversed. Some encryption procedures are too complex to decrypt or require attackers’ help in decryption.
- Pay ransom This is often the dreaded last option. Almost everyone warns against paying ransom malware, including the FBI. However, when it comes down to a single business or person, a decision often has to be made. Paying the ransom is not advisable, and it often promotes subsequent attacks, however, sometimes victims cannot afford to lose their data and opt to pay. For defense and prevention mechanisms, here are a few recommended measures to consider before you are infected.
Deploy gateway defenses
To adequately protect yourself against potential ransomware attacks, you should deploy gateway defense mechanisms such as Intrusion Detection Systems and Intrusion Prevention Systems, Spam filtering and email protection as well as firewall and web application firewall (WAF)
Use Next-generation antivirus software
Using generic or standard antivirus software is a requirement for everyone concerned about their cybersecurity. However, these solutions often do not catch sophisticated ransom malware that is designed to operate stealthily. Leveraging next-generation antivirus is advisable since it can detect malware that does not match the known signatures.
Employee education and anti-phishing tests
Information is a powerful weapon against ransomware attacks. Training employees and general computer users on the security impacts of phishing emails can be impactful in the fight against ransomware.
-
Anti-Ransomware Tools and Solutions
There are many different solutions for both consumers and businesses to protect against ransomware. A basic but necessary layer of protection for consumers is antivirus software. It is important to have a good antivirus installed on your PC, to scan any files that you download to ensure they are safe. One of the best antivirus solutions on the market today is Xcitium Antivirus, which comes in “Free” and “Full” versions, both of which feature a unique “containment” feature, which sequesters any unknown file that a user downloads in a contained, virtual environment, so if the file turns out to be malicious, it cannot do any damage to your system.
Similarly, for businesses, an endpoint protection solution should be able to stop not known and unknown ransomware from gaining access to your system. Therefore, Xcitium’s Advanced Endpoint Protection solution, which uses the same “containment” technology, is an excellent solution to keep enterprises and SMBs ransomware-free.
-
Ransomware news and quick overview
As earlier mentioned, ransomware attacks have seen a significant increase in numbers over the last few years, and the numbers are expected to skyrocket from 2020 through to 2022. A popular trend has started, indicating that ransomware attacks are becoming more targeted. Primary targets remain local governments, educational institutions, and healthcare facilities. New developments also show that Oil and Financial industries have been targeted more in recent years.
Additionally, the ransomware game is changing and will continue to change. More advanced attackers with the ability to build sophisticated and efficient ransomware are opting for the RaaS model to distribute their malware. Novice and averagely skilled cybercriminals are profiting from distributing this malware to users all over the internet. Ransomware-as-a-Service is rising in popularity in underground forums. They are sold for cheap subscription fees to increase their reach.
Some more recent news regarding ransomware:
The Sodinokibi ransomware was making high profile attacks across organizations in 2019 and notably infecting the Albany International Airport as well as Travelex Foreign Exchange Company. Victims of Sodinokibi are threatened by the perpetrators to release the data. This is often scary for companies and victims. It is one thing to lose data, but it is another to have your data publicly available.
The Reading Municipal Light Department faced a ransomware attacks recently. The Electricity Utility, however, opted not to disclose more information regarding the attack. RMLD is a relatively old institution that serves over 29,000 residents in Reading, Massachusetts. In their report, the utility claimed that their data was not compromised and assured their clients of normalcy.
Both Ryuk ransomware and Sodinokibi heavily contributed to the total amount of ransom demanded from ransomware attacks victims. Covaware reported that in the first quarter of 2020, the average ransom payment demanded was $ 111,605. This value has increased by one third from the last recorded value in the last quarter of 2019. Covaware claims that this noticeable increase is as a result of three main ransomware families, Ryuk, Sodinokibi, and Phobos. In the same report, Phobos was listed as the third most notorious ransomware in the first quarter of 2020 -commanding 7.8% of the ransom market share. Phobos primarily attacks small and medium-sized enterprises with vulnerable Remote Desktop Protocol (RDP). Phobos average ransom payment rose to $15,761 from $12,089
Ryuk took second place, commanding 19.6% of the market share. Notably, Ryuk has a significant increase in its average ransom payments rising from $779, 856 in the last quarter of 2019 to $1,339,878 in the first quarter this year. Interestingly, Ryuk recorded the increase, although there was a decline in the size of organizations that it targeted. Covaware, crowned Sodinokibi as the most prevalent of ransomware today. Sodinokibi commanded 26.7% of the market share.
New trends in the ransomware industry have begun to impact other industries. It is reported that cyber insurance claims were the number one reason for claims for Insurers in both 2018 and 2019. This shows a growth rate of more than 100%.
As of May 4, 2020, CPO magazine reported that Cognizant admitted being hit by the Maze ransomware. Cognizant mentioned that they were working with Law enforcement agencies on the matter. Cognizant – which is a Fortune 500 company based in New Jersey, offers IT related services to its customers? This company recorded an annual profit of $16.8 billion in 2019 and conducted business in over 80 countries. The Maze ransomware seems to be on the rise as well, and Cognizant is not the only victim. Maze ransomware has previously been known to hit larger targets including, the US administrator claims, Jackson Plaza, Madison Insurance Group, Chubb Insurance, and Hammersmith Medicines Research.
Ransomware attackers are making significant changes to their business approach. Most of them have realized that data encryption is not enough of a threat to some targets. This is because most businesses today have taken precautionary measures like backing up their data. However, most of these businesses are afraid to expose their data to the public for general reasons. Revealing clients’ payment details, credit card information, confidential business data, and many other forms of sensitive data is not suitable for any business. For this reason, ransomware attacks have begun to exploit this weakness.
In conclusion, ransomware is an imminent threat in 2020, facing all entities. Even though the average computer users may not be under severe threats as before, the increase in the number of sophisticated ransomware is still worrying. Ransomware cost businesses over $8 billion in 2018, and this figure rose in 2019.
You should take part in the fight against ransomware by following the preventive measures recommended above such as, scrutinizing emails and verifying email senders, avoiding email attachments from unknown sources, using email filters and scanners, updating software like Operating systems regularly and finally using anti-ransomware software and tools.




