Secure Auto – Containment
Updated on October 25, 2022, by Xcitium
Xcitium has developed next-generation security based on virtualization to secure organizations from cyber attacks. Similar to the way virtualization transformed the IT datacenter, Xcitium is using OS virtualization to transform the endpoint. Xcitium solves an enterprise’s toughest security challenges.
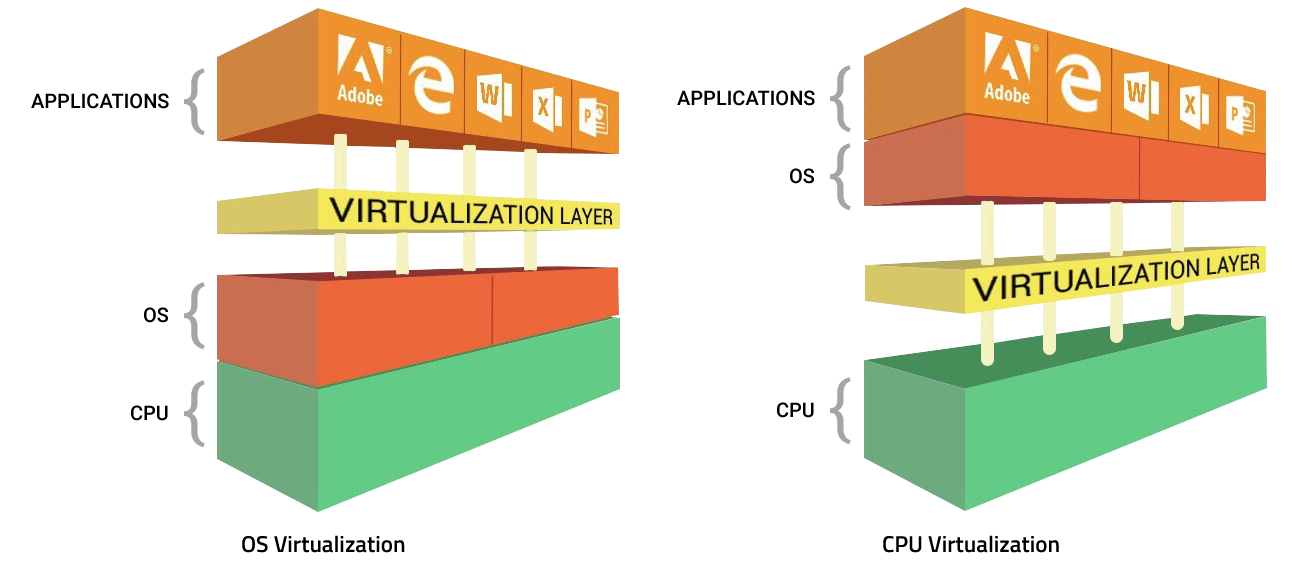
CPU Enforced OS Virtualization
Xcitium’s Secure Auto–containment™ technology uses CPU–enforced OS virtualization with a single container (OS virtualization) model‚ that includes an exact copy of the endpoint machine‚ including the kernel. This is one of the main reasons startup performance is so fast‚ in stark contrast to almost all CPU–draining‚ systems–slowing “sandboxing” or “containers”. In the Xcitium model‚ whenever a process or executable (PE) is run in containment (often referred to as “jailing”)‚ the analysis system sits between the PE and the shadow resources it calls – including CPU‚ memory‚ registry‚ file system and more. If the PE turns out to be malicious code and attempts to exploit the machine‚ that action will occur entirely within the container. It will only affect the container’s shadow resources, not those of the native machine. Neither will it be able to access any of the native resources required actually to compromise the endpoint itself.
Containment: Combining Security and Productivity
This secure container protects the system from any attempted changes or theft of information while allowing the user to continue using their application. For example‚ it provides the granularity required to protect against modern attacks like drive–by download attacks. This type of attack can compromise the entire web browser‚ gain access to system resources and steal information from unsuspecting users. The same attack if targeted against a Xcitium Advanced Endpoint Protection user would only see the very limited set of resources necessary to perform the task on the specific Web–browser tab. Valuable data‚ networks and devices are filtered. When the user resets the container‚ all data including any malware is simply discarded.
CPU Enforced OS Virtualization Conclusion
Xcitium’s Default Deny Platform is both designed to efficiently detect and prevent attacks in our tightly integrated model of Endpoint Protection Platform (EPP), Endpoint Detection & Response (EDR)‚ Secure Auto Containment and global threat intelligence‚ but has also been carefully architected to continue working if any individual component fails or is defeated.
Related Resources




