What We Do for Detection at the Endpoint
Updated on October 25, 2022, by Xcitium
What We Do for Detection at the Endpoint
Xcitium performs extensive detection techniques at the local level to contain unknown files in emulation and prevent infection to the endpoint if they turn out to be malware. From antivirus signatures to application whitelisting and machine learning, to unpackers, detectors, recognizers, and detection of fileless malware, this section defines them all.
What We Do for Detection at the Endpoint: Antivirus for PCI Compliance
The PCI DSS, requirement 5.1.1 states that antivirus solutions: “Detect all known types of malicious software, remove all known types of malicious software, and protect against all known types of malicious software.” Xcitium Antivirus engine detects and cleans virus infections with both standard and advanced capabilities including a general scanner, script scanner, and decompression and static unpack techniques.
Advanced features include PE simulator, script simulator (JavaScript and VBScript), complex document decoding, dynamic unpack and general unpack. Antivirus is a feature of Xcitium Advanced Endpoint Protection along with whitelisting/blacklisting and advanced detection capabilities that together provide multiple layers of protection. Obviously, antivirus alone is not enough to protect the enterprise; however, it has the ability to quarantine and remove known malware from the endpoint.
Xcitium is the world’s largest certificate authority, and is uniquely positioned to have intelligence on known good, digitally signed applications and publishers—more than any competing vendor on the market today. Whitelisting allows us to identify known good files, while blacklisting identifies the known bad, leaving the unknown files for analysis.
Antivirus relies on blacklisting where everything coming into the endpoint from the Internet is assumed to be safe unless it appears on a signature list of bad stuff. Essentially this is the definition of a default allow posture, allowing every new or unknown file or app to run on the endpoint, and it is a key reason why enterprises continue to get infected.Blacklists can’t keep up with the sheer volume of malware today so when they allow unknown files in, some of them are malware. However, blacklisting and whitelisting does help identify known threats and known good apps efficiently to clear the way for other detection methods to identify the rest. This is why Advanced Endpoint Protection has multiple layers of detection, to identify both known bad, known good, and unknown (i.e. zero-day) threats. Xcitium’s dynamic blacklist is constantly updated with global threat intelligence from Valkyrie static and dynamic cloud-based analysis and our 85 million endpoint installations around the world.
Upon detection of a new malware, the industry standard is to create a first signature (CRC signature) quickly to help detect outbreaks. First signatures directly identify the malicious file with a checksum calculation in order to store a short identification of the binary file.This is simple and efficient when you first identify malware for immediate deployment and protection. Then expansive methods are used to develop detections for generic signature, and you can remove first signature.
What We Do for Detection at the Endpoint: Generic Signature and Heuristic Scanning
A virus signature is a string of characters or numbers that antivirus programs are designed to detect. Traditional antivirus signatures are used to check all the .EXE files against a blacklist (known list of viruses) and other types of malware. They also can check if unknown executable files are misbehaving, indicating new malware. Xcitium antivirus performs both generic signature and heuristic scanning at the endpoint to detect virus signatures.
Generic scanning is used to identify new viruses that have been developed from existing virus families while heuristic scanning focuses on detecting new virus signatures. Antivirus programs use heuristics to scan susceptible programs or suspicious applications within a runtime virtual environment. This keeps the vulnerable code from infecting the real world environment. Even in the absence of the latest virus update, this helps the antivirus software detect a new virus, a variant or an altered version of malware.
To enable detection, heuristic scanning creates new signatures each time a new virus is found. Heuristic scanning encompasses more than 250,000 new virus signatures. One signature may contain several virus signatures consisting of algorithms or hashes that uniquely identify a specific virus family. A large number of viruses may share a single signature enabling the antivirus to detect multiple versions during scans.
Antivirus may also include signature replacements or the removal of prior signatures when they are no longer able to properly scan for revised signatures. Viruses are always changing and this is why users are encouraged to install security updates as soon as they are available.
What We Do for Detection at the Endpoint: AI MACHINE LEARNING – VIRUSSCOPE AT THE LOCAL LAYER
Machine learning training techniques combine algorithms and hundreds of static features extracted from files. Very large sets of malicious and clean files are regularly used in machine learning models and refreshed with new files. Machine learning based models, ensure a high degree of accuracy and reduce the management overhead typically associated with exploit validation and response.
Xcitium uses static, dynamic and broader machine learning models to detect malware, Machine learning on the client is done by VirusScope, whereas machine learning in the cloud is handled by Valkyrie. The general method as defined in the “How we detect in the cloud” section is the same at the local level—tracking learned behaviors to detect malware—but there are more resources on the cloud than on the client, and therefore, Valkyrie is more expansive.
Behavioral analysis is used for intrusion detection—concentrating on detecting the characteristics of malware during execution. Behavioral analysis is limited to detection only when the file is performing malware actions.
Precise detectors target specific malware features with high rates of precision to help detect malicious files and minimize false positives. Precise detectors apply heuristic methods to check data patterns in a file. These might include specific opcode sequences, unexpected opcode existences and frequencies, unexpected sections, section contents, imported resources and packing methods etc.
When software vendors create solutions they use generic packers from compilers and installers so users know where to find the data for installation (source files) to decompile or extract data as you would in an archive via generic unpacker. A common example of a generic unpacker is WinZip which follows a standard rfc (generic).It doesn’t need to know about the data inside. Generic packers are also used by malware writers. Executable packing is the most common technique used by computer virus writers to obfuscate malicious code and evade detection by antivirus software. Some malware writers use custom unpackers to keep security vendors from unpacking them.Xcitium has a large set of generic and custom unpackers. Generic unpackers can detect and extract encrypted code from packed executables; therefore, potentially revealing hidden viruses that can be detected by traditional signature-based antivirus software. However, generic unpackers are computationally expensive and scanning large collections of executables looking for virus infections may take several hours or even days. Alternatively, Xcitium uses custom unpackers that are commonly found in malware to identify malicious applications effectively.
Recognizers are activities that Xcitium tracks on the dynamic execution of unknown files in secure auto-containment. To protect the user the file runs in the container (sandbox) while a combination of different recognizers are monitoring it to decide if what the file is doing is good or bad. We have close to a hundred different recognizers.Recognizers have different perspectives on file behavior and look for dynamic behavior signatures. For example one of the recognizers may identify the ransomware CryptoLocker, while another may be looking for behavior to identify a password stealer. They all look for different things. For example, if a password stealer executes in containment it may try to read sensitive files that store the user’s credentials and a recognizer would identify that behavior as password stealer.
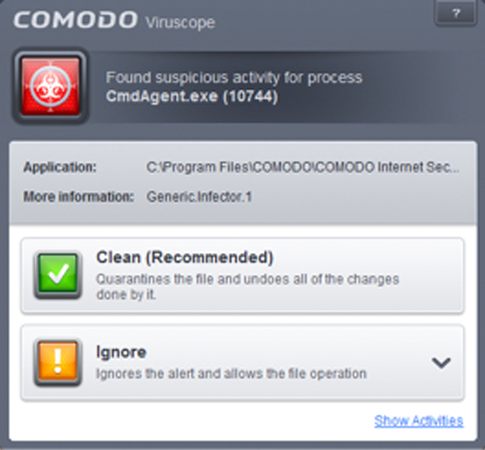 Another example at the local level is a recognizer in VirusScope that detects the following process actions to determine if a file is trusted or malware, such as this example of CryptoLocker behavior:
Another example at the local level is a recognizer in VirusScope that detects the following process actions to determine if a file is trusted or malware, such as this example of CryptoLocker behavior:
- copy and remove (move) self to any folder and add self to autorun in registry
- copy and remove (move) self to autorun folder
- copy and remove (move) self to any folder and create link to self in autorun folder
- copy and remove (move) self and create Windows task to run self
After detection of malware, VirusScope creates a report of activities and saves a copy in the CIS data folder (C:\ProgramData\Xcitium\Cis) and submits a copy to Xcitium servers to share the information. If the detected process is not trusted, VirusScope will show an Alert or perform a default action such as clean up as shown in the screen shot.
What We Do for Detection at the Endpoint: FILELESS MALWARE AT THE ENDPOINT
Fileless malware can’t be detected by traditional antivirus because there is no file signature to match. That is why these infections are called fileless—no files are dropped onto the hard drive. Attackers use fileless malware to avoid being detected by traditional security products for: Privilege escalation – to exploit a vulnerability that will give them administrator access to the system, so they can do whatever they want Information gathering – to harvest as much data about the victim and from the victim’s computer as possible (to be later used in other attacks); Persistence – to keep the malware in the system undetected for the longest time possible. Examples include Advanced Persistent Threats (APTs) that can use any of the following technique:
- Rootkits – this kind of malware masks its existence behind a computer user to gain administrator access. Rootkits often reside in the kernel, thus persisting despite restarts and usual antivirus scans. Its cloaking abilities are uncanny and removal can be almost impossible. Rootkit installation can be automated or an attacker can install it with root or Administrator access. Obtaining this access is a result of direct attack on a system, i.e. exploiting a known vulnerability (such as privilege escalation) or a password (obtained by cracking or social engineering tactics like “phishing”). Once installed, it becomes possible to hide the intrusion as well as to maintain privileged access.The key is the root or administrator access. Full control over a system means that existing software can be modified, including software that might otherwise be used to detect or circumvent it. Some fileless malware hides its presence behind a user- or kernel-level API. A file is present on disk but in a stealth mode. While this isn’t a 100% fileless infection either, it fits here.
- Windows registry malware – newer types of fileless malware are capable of residing in Windows’ registry. The Windows Registry is a database that stores low-level settings for the operating system and certain apps. Malware authors have exploited features such as the Windows thumbnail cache used to store images for Windows Explorer’s thumbnail view.The thumbnail cache acts as a persistence mechanism for the malware. Fileless malware of this type must still enter the victim’s system through a static binary. Most use email as the medium to reach the system. Once the user clicks on the attachment, the malware writes the complete payload file in an encrypted form in the Windows registry hive. It then disappears from the system by deleting itself. Xcitium employs several layers to protect against fileless malware including:
- Antivirus: signature based detection; heuristics-based detection, rootkit detection and real time automatic protection
- Firewall: checks application whitelist for known good apps, checks network traffic for inbound and outbound threats, protects network ports and blocks malicious web sites and software from transmitting data outside your network.
- HIPS: while this is a form of prevention versus detection, Host Intrusion Prevention System (HIPS) automatically protects system-critical files, folders and registry keys to prevent unauthorized modification by malicious programs.
- Secure Auto Containment: runs potentially unsafe applications in OS virtualization environment to prevent damage to endpoints pending trust verdicts from analysis
- Website filtering: allows set up of rules to allow or block access to specific websites
What We Do for Detection at the Endpoint: Emulation at the endpoint
Emulation imitates a certain computer platform or program on another platform or program. In this manner, it is possible to view documents or run programs on a computer not designed to do so. An emulator is itself a program that creates an extra layer between an existing computer platform (host platform) and the platform to be reproduced (target platform).
Because emulation programs implement functionality in software, they provide greater flexibility for detecting malware. Xcitium uses emulation to run unknown files safely in a sandbox environment. This is part of our default deny posture with secure auto containment of unknown files. We don’t let a file run on the host unless we know it is safe. Other security solutions do the opposite with default allow postures they don’t let known malware run but assume everything else is safe and let it run on the host. Since new malware begins as unknown files, this is how endpoints become infected. By running in virtualization (emulation) it is possible to view documents or run programs in secure auto-containment to determine if a file is good or bad before allowing it to run on the endpoint.
There are no performance hits because Xcitium OS virtualization technology is extremely lightweight, has no CPU dependencies and is completely application agnostic. One of the advantages of virtualization is that programs in virtual machines can run at essentially native speed. This is one of the reasons Xcitium developed CPU enforced OS virtualization for security with usability. Xcitium can automatically contain unknown files in a sandbox where they can be used safely and analyzed in a safe run-time environment and do no damage if they are malware. 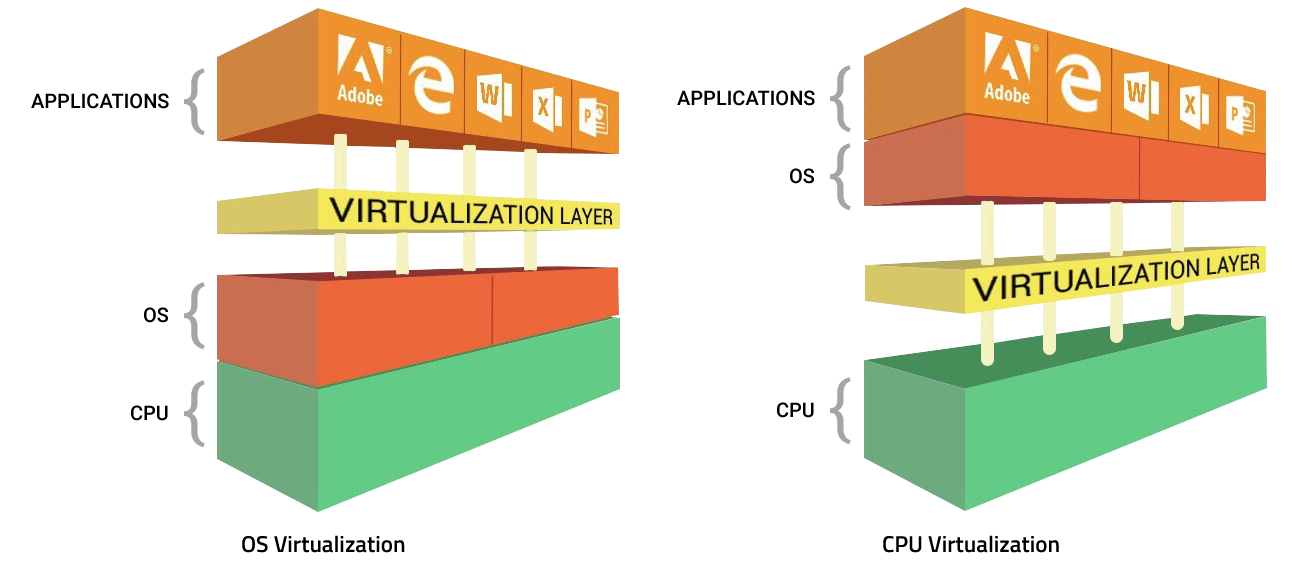
Related Resources




